Security researchers at Bitdefender have discovered four vulnerabilities impacting multiple versions of WebOS, the operating system used in LG smart TVs.
The flaws enable varying degrees of unauthorized access and control over affected models, including authorization bypasses, privilege escalation, and command injection.
The potential attacks hinge on the ability to create arbitrary accounts on the device using a service that runs on ports 3000/3001, which is available for smartphone connectivity, using a PIN.
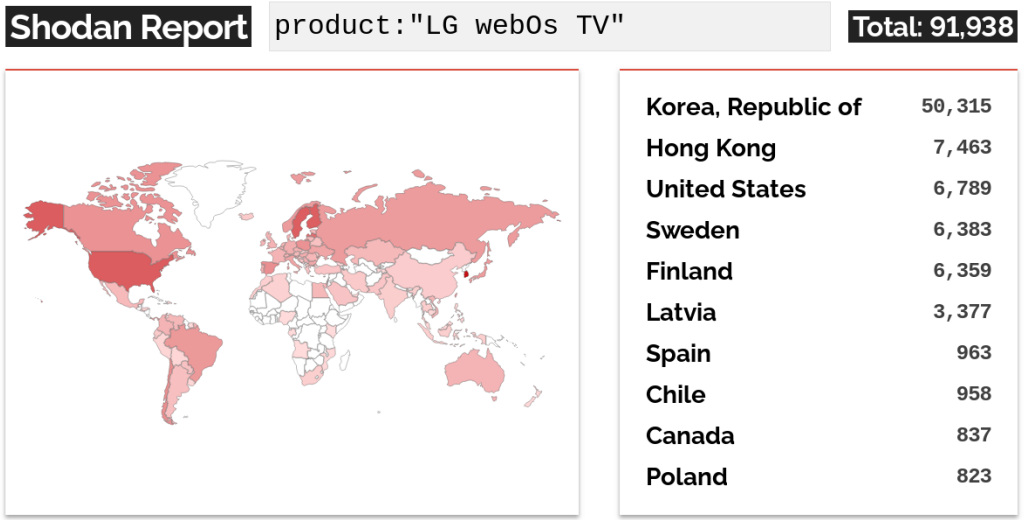
Bitdefender explains that although the vulnerable LG WebOS service is supposed to be used only in local area networks (LAN) settings, Shodan internet scans show 91,000 exposed devices that are potentially vulnerable to the flaws.
The four flaws are summarized as follows:
- CVE-2023-6317 allows attackers to bypass the TV’s authorization mechanism by exploiting a variable setting, enabling the addition of an extra user to the TV set without proper authorization.
- CVE-2023-6318 is an elevation of privilege vulnerability that allows attackers to gain root access following the initial unauthorized access provided by CVE-2023-6317.
- CVE-2023-6319 involves operating system command injection via manipulation of a library responsible for displaying music lyrics, allowing execution of arbitrary commands.
- CVE-2023-6320 permits authenticated command injection by exploiting the com.webos.service.connectionmanager/tv/setVlanStaticAddress API endpoint, enabling command execution as the dbus user, which has similar permissions to the root user.
The vulnerabilities impact webOS 4.9.7 – 5.30.40 on LG43UM7000PLA, webOS 04.50.51 – 5.5.0 on OLED55CXPUA, webOS 0.36.50 – 6.3.3-442 on OLED48C1PUB, and webOS 03.33.85 – 7.3.1-43 on OLED55A23LA.
Bitdefender reported its findings to LG on November 1, 2023, but it took the vendor until March 22, 2024, to release the related security updates.
Though LG TVs alert users when important WebOS updates are available, those can be postponed indefinitely. Therefore, impacted users should apply the update by going to the TV’s Settings > Support > Software Update, and selecting “Check for Update.”
Applying WebOS updates automatically when available can be enabled from the same menu.
Though TVs are less critical in terms of security, the severity of remote command execution remains potentially significant in this case as it could give attackers a pivot point to reach other, more sensitive devices connected to the same network.
Moreover, smart TVs often have applications that require accounts, like streaming services, which the attacker could potentially steal to take control of those accounts.
Finally, vulnerable TVs can be compromised by malware botnets that enlist them in distributed denial of service (DDoS) attacks or used for cryptomining.














