Flare researchers monitoring underground Telegram channels and cybercrime forums have observed threat actors rapidly sharing proof-of-concept exploits, offensive tools, and stolen administrator credentials related to recently disclosed SmarterMail vulnerabilities, providing insight into how quickly attackers weaponize new security flaws.
The activity occurred within days of the vulnerabilities being disclosed, with threat actors sharing and selling exploit code and compromised access tied to CVE-2026-24423 and CVE-2026-23760, critical flaws that enable remote code execution and authentication bypass on exposed email servers.
These vulnerabilities have since been confirmed in real-world attacks, including ransomware campaigns, highlighting how attackers increasingly target email infrastructure as an initial access point into corporate networks, allowing them to move laterally and establish persistent footholds.
CVE-2026-24423 and CVE-2026-23760: Critical RCE and Auth Bypass Flaws
Multiple recently disclosed SmarterMail vulnerabilities created a perfect storm that made the platform highly attractive to attackers. Among them, CVE-2026-24423 stands out as a critical unauthenticated remote code execution flaw affecting versions prior to Build 9511.
With a CVSS score of 9.3 and no user interaction required, the flaw is particularly suited for automation, large-scale scanning, and mass exploitation campaigns.
In parallel, additional vulnerabilities CVE-2026-23760 (CVSS 9.3) include authentication bypass and password reset logic flaws. It allows attackers to reset administrator credentials or gain privileged access to the platform. Research also shows that attackers were quickly reverse-engineering patches to identify and weaponize these weaknesses within days of release.
When combined, these issues enabled full server takeover scenarios, where attackers could move from application-level access to operating system control and potentially domain-level compromise in connected environments.
From an attacker’s perspective, this combination is ideal: SmarterMail is a network-exposed service, often holds a high trust position inside enterprise environments, and in many cases is monitored less aggressively than endpoint systems protected by EDR.
Once proof-of-concept exploit code becomes available, exploitation can be rapidly operationalized – meaning the timeline from vulnerability disclosure to ransomware deployment can shrink to days.
SmarterTools Breached by Own Product Flaw, Ransomware Groups Follow
Recent incidents demonstrate exactly how this pipeline plays out.
According to a SmarterTools report, SmarterTools was breached in January 2026 after attackers exploited an unpatched SmarterMail server running on an internal VM that was exposed inside their network.
The compromised environment included office and lab networks and a data-center segment connected through Active Directory, where attackers moved laterally and impacted around a dozen Windows servers.
The company shut down the affected infrastructure, restored systems from backup, rotated credentials, and removed some Windows/AD dependencies. Having said that, it was reported that core customer services and data were unaffected. Attackers gained an internal network foothold and attempted typical ransomware-style post-exploitation actions; it wasn’t successful, thanks to network segmentation.
In another investigation published by Bleeping Computer, ransomware operators gained initial access through SmarterMail vulnerabilities and waited before triggering encryption payloads, a classic affiliate behavior pattern.
This pattern is important:
- Initial access via email server vulnerability
- Credential harvesting or token extraction
- Lateral movement via Active Directory
- Persistence via scheduled tasks or DFIR tool abuse
- Ransomware deployment after staging period
Some campaigns have been linked to the Warlock ransomware group, with overlaps observed with nation-state-aligned activity clusters.
Flare monitors underground forums and Telegram channels where threat actors share PoCs, exploits, and compromised credentials within hours of disclosure.
Get early warning when your infrastructure is discussed or targeted by ransomware operators.
Start Free Trial
Email Servers: Identity Infrastructure Attackers Target First
Email servers sit at a unique intersection of trust and visibility.
They often provide:
- Domain authentication tokens
- Password reset capabilities
- External communication channels
- Access to internal contact graphs
- Integration with identity and directory services
Attackers understand that email ecosystems rely on multi-component authentication chains where a single weak link can break overall trust. Compromise the email infrastructure and you effectively compromise identity.
1,200+ Vulnerable Servers Identified on Shodan
We found ~34,000 servers on Shodan with indications of running SmarterMail. Out of the 34,000, there were 17,754 unique servers.
A further inspection of these servers shows that 1,185 are vulnerable to authentication bypass or RCE flaws. Other publications talk about ~6,000 vulnerable servers.
A geo-location analysis of these 1,185 servers shows US dominance:
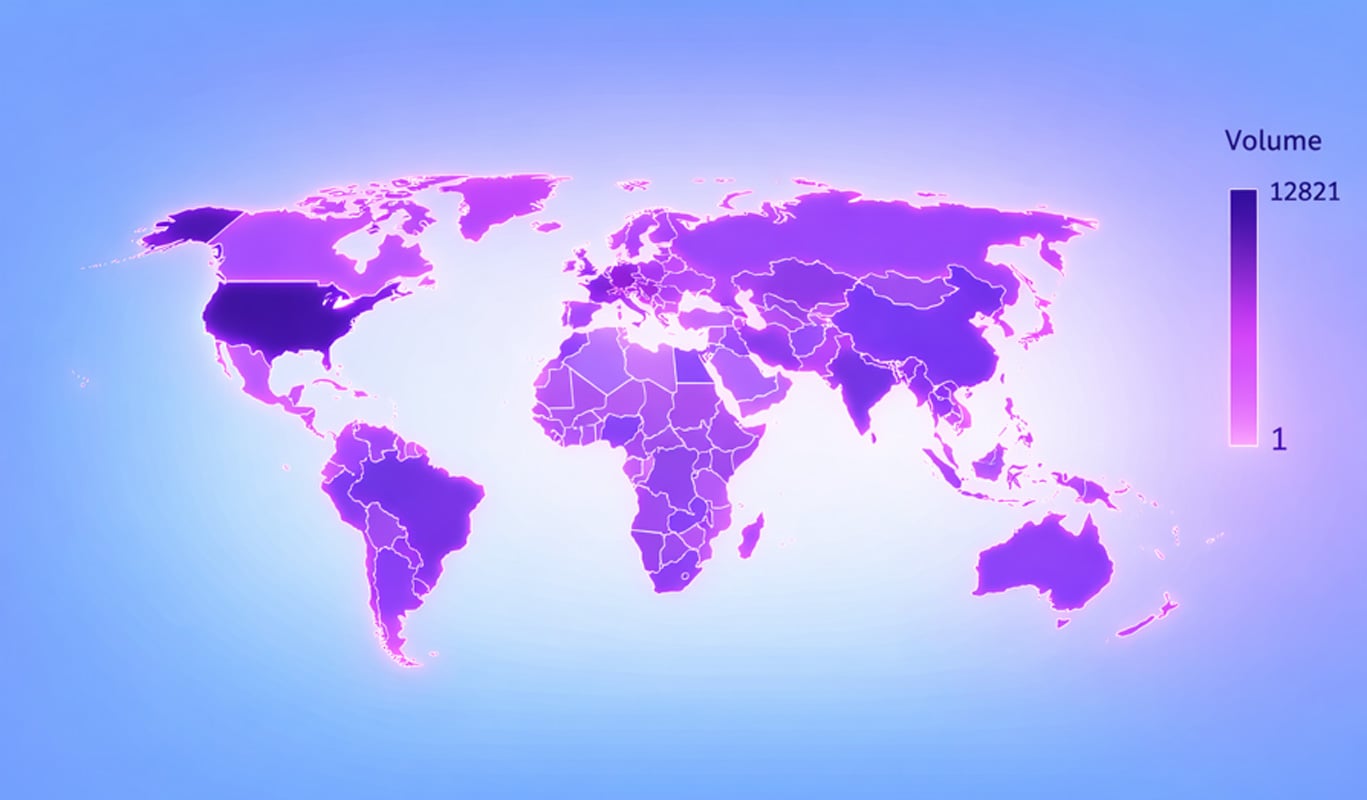
A further analysis of the ISPs and Organizations shows a very diverse distribution of open SmarterMail servers, many self-hosted admin panels, shared hosting, VPS providers, and general-purpose cloud networks, typical of deployment by individuals rather than organizations.
This may indicate that after the strong security hype over the past weeks, organizations were quick to react and block this attack surface.
Underground Forums Share Exploits Within Days of Disclosure
The underground ecosystems are fast to react to such publications. The CVEs were published around the beginning of January, and on the same day, there were mentions and references to these vulnerabilities. To date, we’ve seen dozens of publications and references to these vulnerabilities.
This is normal underground behavior when it comes to critical vulnerabilities.
We have also seen some more malicious references. A few days after the first publication, there were references to Proof of Concept or exploit of the vulnerabilities. For instance, an Arabic-speaking Telegram channel shows PoC.
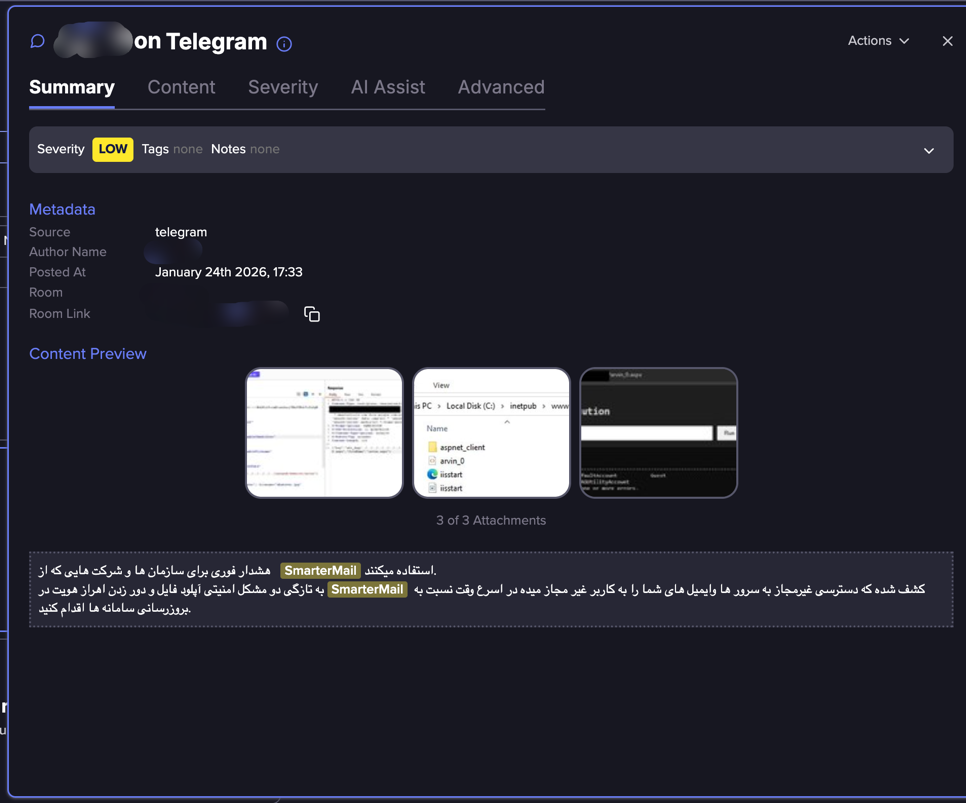
You can also see how the threat actor is showing proof of concept:
And another threat actor is showing a proof of concept to this vulnerability:
In a Spanish-speaking Telegram group, we saw references to an Offensive Security Tool:
On another Telegram group, we saw a data dump of admin credentials highlighted as it comes from a compromised SmarterMail server:
When accessing one of the links, you can indeed see a long list of admin credentials and the domains (or login) to which they belong.
CISA Confirms Active Exploitation in Ransomware Campaigns
These vulnerabilities were published in the beginning of 2026, CISA added CVE-2026-24423 to the Known Exploited Vulnerabilities catalog in the beginning of February 2026, after confirming active ransomware exploitation.
This confirms that attackers are quick to exploit newly discovered critical RCE- related vulnerabilities:
- Vulnerability disclosure
- PoC written and released
- Mass scanning operation
- Weaponization: Data exfiltration, Ransomware etc.
Timeline shrinking from months/weeks to days.
How to Protect Email Infrastructure From Ransomware Access
Many organizations still treat email servers as “ONLY application infrastructure”. Well, they are not!
They are identity infrastructures that enable many follow-up attack vectors, as well as containing secrets and business logic. Defensive priorities should include:
- Patch Urgency: Critical email server vulnerabilities should be treated like domain controller vulnerabilities.
- Identity Telemetry: Organizations should monitor these environments for:
- Admin password resets
- API calls to external hosts
- Unexpected outbound HTTP from mail servers
- Network Segmentation: Email infrastructure should never have unrestricted access to internal networks.
- Threat Hunting Practice:
- API abuse patterns
- Scheduled task persistence
- Unexpected tooling like DFIR frameworks or remote admin tools
Email Servers Are Identity Infrastructure—Secure Them Accordingly
The SmarterMail cases show once again how modern cybercrime operations are quick to add newly discovered initial access to their ongoing operation.
It also re-emphasizes the critical role email servers take in the modern organization:
- Identity brokers
- Trust anchors
- Business logic
- Invaluable reconnaissance data for follow-up cybercrime
Organizations that continue treating them as just “messaging systems” will remain vulnerable to this new generation of intrusion pipelines.
Learn more by signing up for our free trial.
Sponsored and written by Flare.














