A security researcher has released a partial proof of concept exploit for a vulnerability in the FortiWeb web application firewall that allows a remote attacker to bypass authentication.
The flaw was reported responsibly to Fortinet and is now tracked as CVE-2025-52970. Fortinet released a fix on August 12.
Security researcher Aviv Y named the vulnerability FortMajeure and describes it as a “silent failure that wasn’t meant to happen.” Technically, it is an out-of-bounds read in FortiWeb’s cookie parsing that lets an attacker set the Era parameter to an unexpected value.
This causes the server to use an all-zero secret key for session encryption and HMAC signing, making forged authentication cookies trivial to create.
Exploitation results in a full authentication bypass, letting the attacker impersonate any active user, including an administrator.
To exploit CVE-2025-52970 successfully, the target user must have an active session during the attack, and the adversary must brute-force a small numeric field in the cookie.
The brute-forcing requirement comes from a field in the signed cookie that is validated by the function refresh_total_logins() (in libncfg.so).
This field is an unknown number that the attacker must guess, but the researcher notes that the range is usually not above 30, makingg it a tiny search space of roughly 30 requests.
Because the exploit uses the all-zero key (due to the Era bug), each guess can be tested instantly by checking if the forged cookie is accepted.
The issue impacts FortiWeb 7.0 to 7.6, and was fixed in the below versions:
- FortiWeb 7.6.4 and later
- FortiWeb 7.4.8 and later
- FortiWeb 7.2.11 and later
- FortiWeb 7.0.11 and later
Fortinet says in the bulletin that FortiWeb 8.0 releases aren’t impacted by this issue, so there’s no action that needs to be taken there.
The security bulletin lists no workarounds or mitigation advice, so upgrading to a safe version is the only recommended effective action.
Fortinet’s CVSS severity score of 7.7 can be deceptive, as it derives from “high attack complexity” due to the brute-forcing requirement. In practice though, the brute-forcing part is simple and quick to perform.
The researcher shared a PoC output, showing admin impersonation on a REST endpoint. However, he withheld the complete exploit that also covers connecting to the FortiWeb CLI via /ws/cli/open.
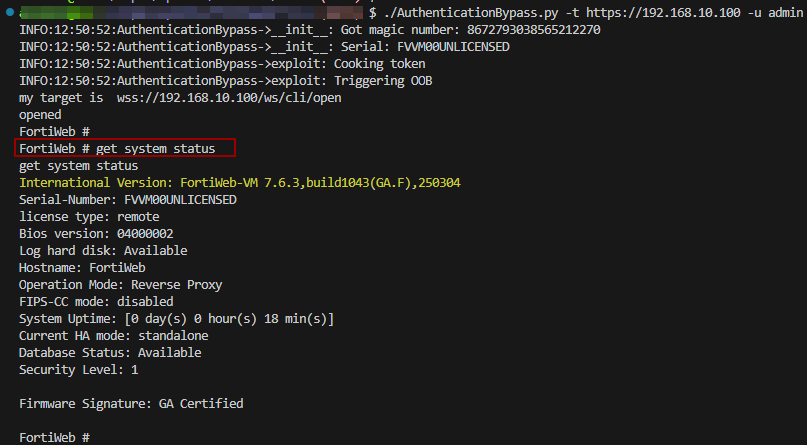
However, Aviv Y promised to publish the complete exploitation details later, as the vendor’s advisory has been released only recently. The researcher made this decistion to allow system administrators more time to apply the fix.
The published details demonstrate the core of the issue but are not enough even for knowledgeable attackers to infer the rest and develop a full weaponized chain, the researcher told BleepingComputer.
He explained that attackers would have to reverse engineer the format of the fields in the session, which is impractical given that Fortinet has its own data structures.
Despite that, immediate action must be taken to mitigate the issue as hackers follow these announcements closely and get ready to pull the trigger when full PoCs are out.
Aviv Y told BleepingComputer he has not decided on the date for publishing the exploit but plans to give defenders time to respond to the risk.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.













