A vulnerability tracked as CVE-2024-31497 in PuTTY 0.68 through 0.80 could potentially allow attackers with access to 60 cryptographic signatures to recover the private key used for their generation.
PuTTY is a popular open-source terminal emulator, serial console, and network file transfer application that supports SSH (Secure Shell), Telnet, SCP (Secure Copy Protocol), and SFTP (SSH File Transfer Protocol).
System administrators and developers predominantly use the software to remotely access and manage servers and other networked devices over SSH from a Windows-based client.
The vulnerability tracked as CVE-2024-31497 was discovered by Fabian Bäumer and Marcus Brinkmann of the Ruhr University Bochum and is caused by how PuTTY generates ECDSA nonces (temporary unique cryptographic numbers) for the NIST P-521 curve used for SSH authentication.
Specifically, there’s a bias due to PuTYY’s use of a deterministic way to generate these numbers to compensate for the lack of a robust cryptographic random number generator on specific Windows versions.
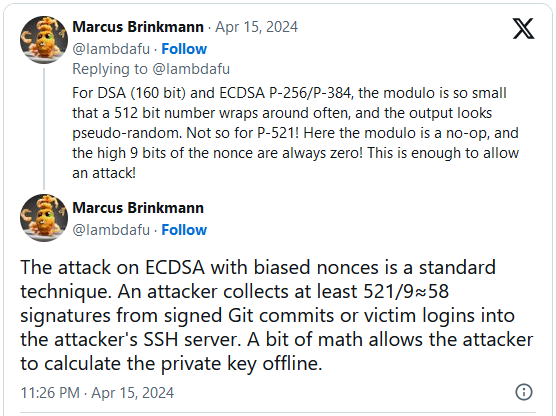
“PuTTY’s technique worked by making a SHA-512 hash and then reducing it mod q, where q is the order of the group used in the DSA system. For integer DSA (for which PuTTY’s technique was originally developed), q is about 160 bits; for elliptic-curve DSA (which came later), it has about the same number of bits as the curve modulus, so 256 or 384 or 521 bits for the NIST curves.”
“In all of those cases except P521, the bias introduced by reducing a 512-bit number mod q is negligible. But in the case of P521, where q has 521 bits (i.e. more than 512), reducing a 512-bit number mod q has no effect at all – you get a value of k whose top 9 bits are always zero.” – PuTTY security advisory.
The main repercussion of recovering the private key is that it allows unauthorized access to SSH servers or sign commits as the developer.
Exploiting CVE-2024-31497
A digital signature is created using a user’s private key and verified by the corresponding public key on the server, ensuring the user’s identity and the communication’s security.
Brinkmann explained on X that attackers require 58 signatures to calculate a target’s private key, which they can acquire either by collecting them from logins to an SSH server they control or is compromised, or from signed Git commits.
Collecting signatures from an SSH server is not as critical as it would mean the server itself is already compromised, and thus, the threat actor has broad access to the operating system.
However, Bäumer told BleepingComputer that the second method of harvesting signatures from public commits is far more practical for attackers.
There are instances where this vulnerability can be exploited without the need to compromise a server in advance.
One such case is the use of SSH keys for signing Git commits. A common setup involves using Pageant, the ssh-agent of PuTTY, locally and forwarding the agent to a development host.
Here, you configure Git to use OpenSSH to sign Git commits with the SSH key provided by Pageant. The signature is then generated by Pageant, making it susceptible to private key recovery.
This is particularly concerning as git signatures may be publicly accessible, for example, if the commit is pushed to a public repository on GitHub.
❖ Fabian Bäumer
Flaw fixed, other software impacted
The developers fixed the vulnerability in PuTTY version 0.81, which abandons the previous k-generation method and switches to the RFC 6979 technique for all DSA and ECDSA keys.
However, it is noted that any P521 private keys generated using the vulnerable version of the tool should be considered unsafe and replaced by new, secure keys.
The following software that uses the vulnerable PuTTY is confirmed as impacted:
- FileZilla 3.24.1 – 3.66.5 (fixed in 3.67.0)
- WinSCP 5.9.5 – 6.3.2 (fixed in 6.3.3)
- TortoiseGit 2.4.0.2 – 2.15.0 (fixed in 2.15.0.1)
- TortoiseSVN 1.10.0 – 1.14.6 (mitigation possible by configuring TortoiseSVN to use Plink from the latest PuTTY 0.81 release)
There are likely more software tools impacted by CVE-2024-31497, depending on which PuTTY version they incorporate. Therefore, users are advised to check their tools and take preventive action as needed.