Researchers have released proof-of-concept (PoC) exploits for a critical Citrix NetScaler vulnerability, tracked as CVE-2025-5777 and dubbed CitrixBleed2, warning that the flaw is easily exploitable and can successfully steal user session tokens.
The CitrixBleed 2 vulnerability, which affects Citrix NetScaler ADC and Gateway devices, allows attackers to retrieve memory contents simply by sending malformed POST requests during login attempts.
This critical flaw is named CitrixBleed2 as it closely resembles the original CitrixBleed (CVE-2023-4966) bug from 2023, which was exploited by ransomware gangs and in attacks on governments to hijack user sessions and breach networks.
In technical analyses first released by watchTowr and then Horizon3, researchers confirmed that the vulnerability can be exploited by sending an incorrect login request, where the login= parameter is modified so it’s sent without an equal sign or value.
This causes the NetScaler appliance to display the memory contents up to the first null character in the
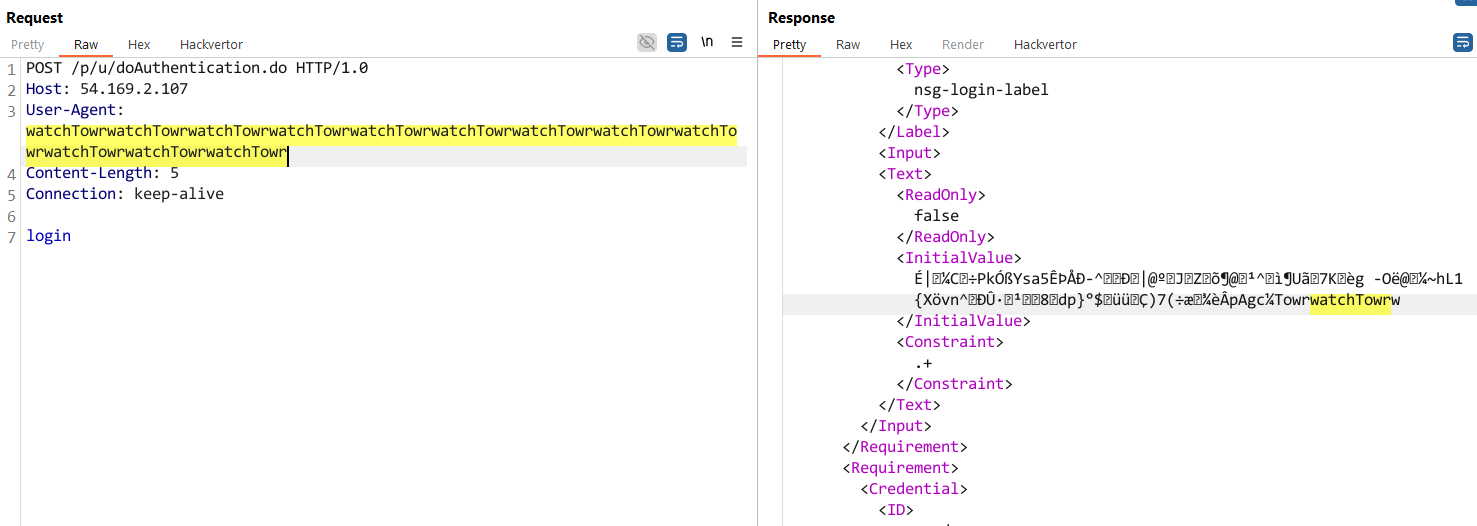
The flaw is caused by the use of the snprintf function along with a format string containing the %.*s format string.
“The %.*s format tells snprintf: “Print up to N characters, or stop at the first null byte (�) – whichever comes first.” That null byte eventually appears somewhere in memory, so while the leak doesn’t run indefinitely, you still get a handful of bytes with each invocation,” explains watchTowr’s report.
“So, every time you hit that endpoint without the =, you pull more uninitialized stack data into the response.”
According to Horizon3, each request leaks approximately 127 bytes of data from data, allowing attackers to perform repeated HTTP requests to extract additional memory contents until they find the sensitive data they are looking for.
While the attempts by WatchTowr were unsuccessful, Horizon3 demonstrates in the video below that they could exploit this flaw to steal user session tokens.
In addition to NetScaler endpoints, Horizon3 states that the flaw can also be exploited against configuration utilities used by administrators.
Exploited or not?
Citrix continues to state that the flaw is not actively being exploited, and when BleepingComputer previously inquired about its status, the company referred us to a blog post about the vulnerability.
“Currently, there is no evidence to suggest exploitation of CVE-2025-5777,” reads the blog post.
However, a June report by cybersecurity firm ReliaQuest indicates that there is evidence that CVE-2025-5777 may have been exploited in attacks, with the company seeing an increase in user session hijacks.
Furthermore, security researcher Kevin Beaumont disputes Citrix’s statement, saying the vulnerability has been actively exploited since mid-June, with attackers leveraging the bug to dump memory and hijack sessions.
He highlighted the following indicators of compromise:
- In Netscaler logs, repeated POST requests to *doAuthentication* – each one yields 126 bytes of RAM
- In Netscaler logs, requests to doAuthentication.do with “Content-Length: 5”
- In Netscaler user logs, lines with *LOGOFF* and user = “*#*” (i.e. # symbol in the username). RAM is played into the wrong field.
“Worth noting I was only able to find exploitation activity due to the WatchTowr and Horizon3 write ups,” warned Beaumont.
“Citrix support wouldn’t disclose any IOCs and incorrectly claimed (again — happened with CitrixBleed) that no exploitation [was] in the wild. Citrix have gotta get better at this, they’re harming customers.”
Citrix has released patches to address CVE-2025-5777, and all organizations are strongly urged to apply them immediately now that public exploits are available.
While Citrix recommends terminating all active ICA and PCoIP sessions, administrators should first review existing sessions for any suspicious activity before doing so.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.













