Threat actors have been exploiting a zero-day vulnerability in legacy Sitecore deployments to deploy WeepSteel reconnaissance malware.
The flaw, tracked under CVE-2025-53690, is a ViewState deserialization vulnerability caused by the inclusion of a sample ASP.NET machine key in pre-2017 Sitecore guides.
Some customers reused this key in production, allowing attackers with knowledge of the key to craft valid, but malicious ‘_VIEWSTATE’ payloads that tricked the server into deserializing and executing them, leading to remote code execution (RCE).
The flaw isn’t a bug in ASP.NET itself, but a misconfiguration vulnerability created by reusing publicly documented keys that were never meant for production.
Exploitation activity
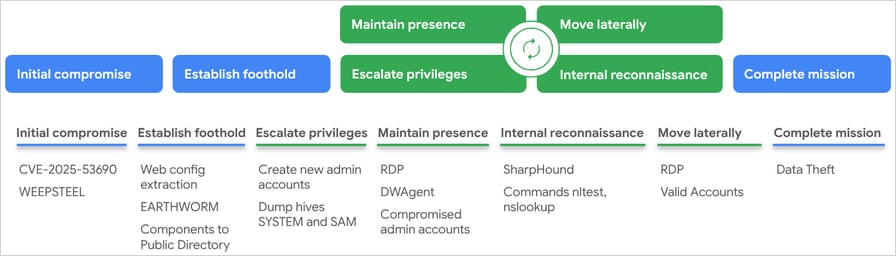
Mandiant researchers, who discovered the malicious activity in the wild, report that threat actors have been leveraging the flaw in multi-stage attacks.
The attackers target the ‘/sitecore/blocked. aspx’ endpoint, which contains an unauthenticated ViewState field, and achieve RCE under the IIS NETWORK SERVICE account by leveraging CVE-2025-53690.
The malicious payload they drop is WeepSteel, a reconnaissance backdoor that gathers system, process, disk, and network information, disguising its exfiltration as standard ViewState responses.

Mandiant observed the execution of reconnaissance commands on compromised environments, including whoami, hostname, tasklist, ipconfig /all, and netstat -ano.
In the next stage of the attack, the hackers deployed Earthworm (a network tunneling and reverse SOCKS proxy), Dwagent (a remote access tool), and 7-Zip, which is used to create archives of the stolen data.
Subsequently, they escalated their privileges by creating local administrator accounts (‘asp$,’ ‘sawadmin’), cached (SAM and SYSTEM hives) credentials dumping, and attempted token impersonating via GoTokenTheft.
Persistence was secured by disabling password expiration for these accounts, giving them RDP access, and registering Dwagent as a SYSTEM service.
Mitigating CVE-2025-53690
CVE-2025-53690 impacts Sitecore Experience Manager (XM), Experience Platform (XP), Experience Commerce (XC), and Managed Cloud, up to version 9.0, when deployed using the sample ASP.NET machine key included in pre-2017 documentation.
XM Cloud, Content Hub, CDP, Personalize, OrderCloud, Storefront, Send, Discover, Search, and Commerce Server are not impacted.
Sitecore published a security bulletin in coordination with Mandiant’s report, warning that multi-instance deployments with static machine keys are also at risk.
The recommended actions for potentially impacted administrators are to immediately replace all static
In general, it is recommended to adopt regular static machine key rotation as an ongoing security measure.
More information on how to protect ASP.NET machine keys from unauthorized access can be found here.

46% of environments had passwords cracked, nearly doubling from 25% last year.
Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.














