Hackers are exploiting a new, undocumented vulnerability in the implementation of the cryptographic algorithm present in Gladinet’s CentreStack and Triofox products for secure remote file access and sharing.
By leveraging the security issue, the attackers can obtain hardcoded cryptographic keys and achieve remote code execution, researchers warn.
Although the new cryptographic vulnerability does not have an official identifier, Gladinet notified customers about it and advised them to update the products to the latest version, which, at the time of the communication, had been released on November 29.
The company also provided customers with a set of indicators of compromise (IoCs), indicating that the issue was being exploited in the wild.
Security researchers at managed cybersecurity platform Huntress are aware of at least nine organizations targeted in attacks leveraging the new vulnerability along with an older one tracked as CVE-2025-30406 – a local file inclusion flaw that allows a local attacker to access system files without authentication.
Hardcoded cryptographic keys
Using the IoCs from Gladinet, Huntress researchers were able to determine where the flaw was and how threat actors are leveraging it.
Huntress found that the issue stems from the custom implementation of the AES cryptographic algorithm in Gladinet CentreStack and Triofox, where the encryption key and Initialization Vector (IV) were hardcoded inside the GladCtrl64.dll file and could be easily obtained.
Specifically, the key values were derived from two static 100-byte strings of Chinese and Japanese text, which were identical across all product installations.
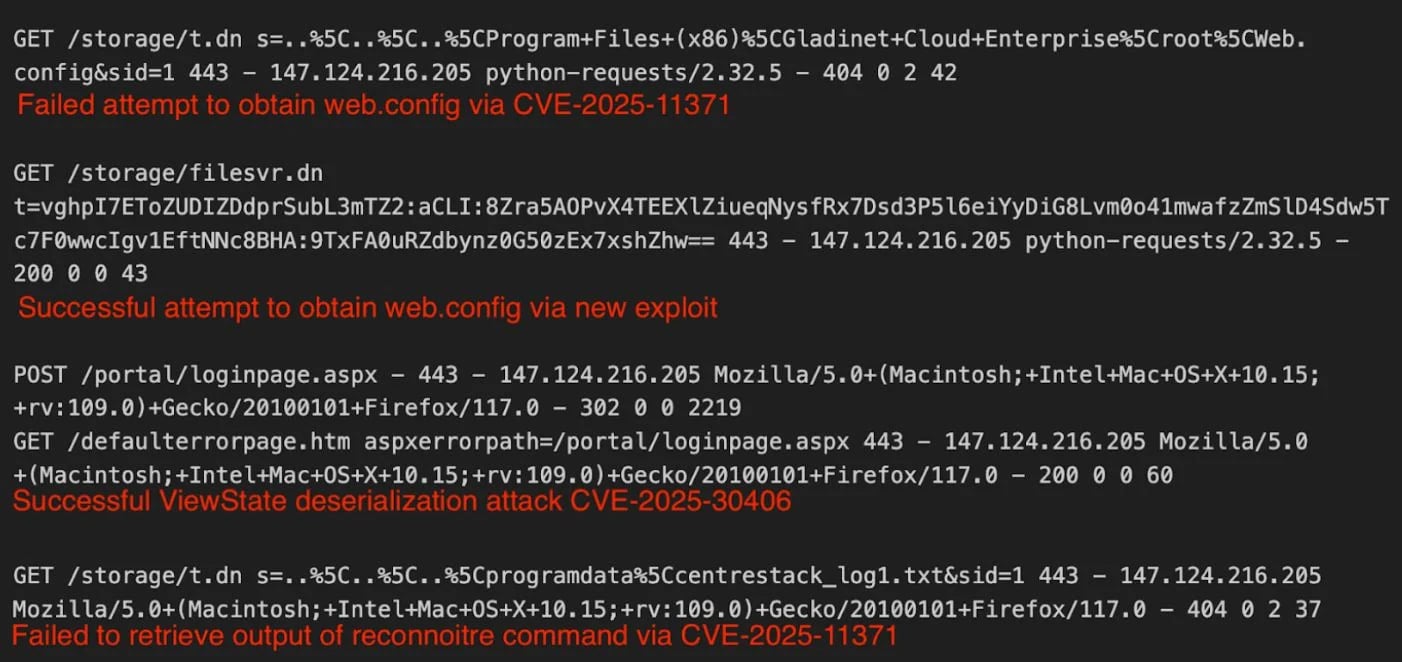
The flaw lies in the processing of the ‘filesvr.dn’ handler, which decrypts the ‘t’ parameter (Access Ticket) using those static keys, Huntress explains.
Anyone extracting those keys could decrypt the Access Tickets containing file paths, usernames, passwords, and timestamps, or create their own to impersonate users and instruct servers to return any file on the disk.
“Because these keys never change, we could extract them from memory once and use them to decrypt any ticket generated by the server or worse, encrypt our own,” the researchers say.
Huntress observed that Access Tickets were forged using hardcoded AES keys and setting the timestamp to year 9999, so the ticket never expires.
The attackers next requested the server’s web.config file. Since it contains the machineKey, they were able to use it to trigger remote code execution through a ViewState deserialization flaw.
Besides an attacking IP address, 147.124.216[.]205, no specific attribution has been made for those attacks.
Regarding the targets, Huntress confirmed nine organizations as of December 10, from various sectors, including healthcare and technology.
Users of Gladinet CentreStack and Triofox are recommended to upgrade to version 16.12.10420.56791 (released on December 8) as soon as possible and also rotate the machine keys.
Additionally, it is recommended to scan logs for the ‘vghpI7EToZUDIZDdprSubL3mTZ2’ string, which is associated with the encrypted file path, and is considered the only reliable indicator of compromise.
Huntress provides mitigation guidance in its report, along with indicators of compromise that defenders can use to protect their environments or determine if they were breached.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.














