The Black Basta ransomware operation is suspected of exploiting a Windows privilege escalation vulnerability (CVE-2024-26169) as a zero-day before a fix was made available.
The flaw is a high-severity issue (CVSS v3.1: 7.8) in the Windows Error Reporting Service, allowing attackers to elevate their privileges to SYSTEM.
Microsoft fixed the flaw on March 12, 2024, via its monthly Patch Tuesday updates, while its status on the vendor’s page shows no active exploitation.
A report by Symantec says that CVE-2024-26169 has been actively exploited by the Cardinal cybercrime group (Storm-1811, UNC4394), the operators of the Black Basta gang, noting that there’s a good chance it was leveraged as a zero-day.
Exploiting CVE-2024-26169
Symantec investigated an attempted ransomware attack where an exploit tool for CVE-2024-26169 was deployed following an initial infection by the DarkGate loader, which Black Basta has been using since the QakBot takedown.
The analysts believe the attackers are linked to Black Basta because they used batch scripts that masquerade as software updates designed to run malicious commands and establish persistence on compromised systems, a common tactic for this group.
The observed exploit tool leveraged the fact that the Windows file werkernel.sys uses a null security descriptor when creating registry keys.
The tool exploits this to create a registry key (HKLMSoftwareMicrosoftWindows NTCurrentVersionImage File Execution OptionsWerFault.exe) and sets the “Debugger” value to its own executable pathname, allowing it to launch a shell with SYSTEM privileges.
Below is a demonstration of BleepingComputer testing the exploit on a Windows 11 device that only has the Windows security updates from February installed, before Microsoft fixed the flaw in March.
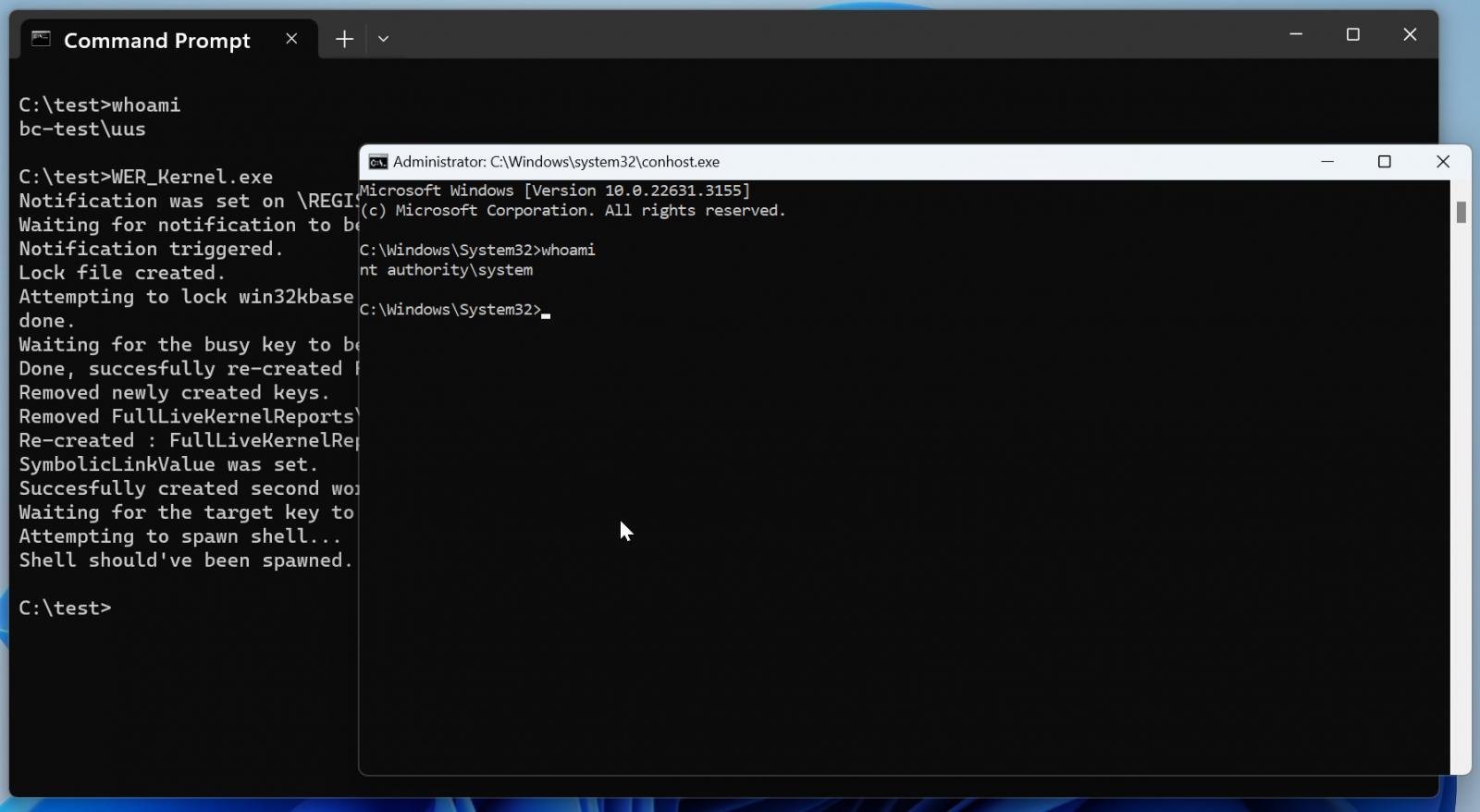
A fascinating aspect of Symantec’s findings is that one variant of the exploit tool has a compilation timestamp dated February 27, 2024, while a second sample was built even earlier, on December 18, 2023.
This means that Black Basta had a working exploit tool between 14 and 85 days before Microsoft eventually pushed a fix for the privilege elevation issue.
While timestamps in portable executables can be modified, as Symantec admits, making the finding inconclusive regarding whether zero-day exploitation occurred, there appears to be little motivation for the attackers to falsify the timestamps, so this scenario is unlikely.
Black Basta, a ransomware operation believed to be linked to the now-defunct Conti cybercrime syndicate, has previously demonstrated expertise in abusing Windows tools and an in-depth understanding of the platform.
A May 2024 advisory from CISA and the FBI highlighted Black Basta’s high-volume activity, holding its affiliates responsible for 500 breaches since April 2022, the time of its launch.
Blockchain analytics firm Elliptic reported in November 2023 that the ransomware operation had made over $100 million in ransom payments.
To mitigate Black Basta’s use of this vulnerability, it is essential to apply the latest Windows security update and follow the guidelines shared by CISA.














