Today’s threat landscape, attack surfaces are expanding faster than most security teams can track. Every new cloud asset, exposed API, forgotten subdomain, or misconfigured service becomes an opportunity for an attacker to exploit.
Modern threat actors are leveraging Attack Surface Management (ASM) to map out your digital footprint before you even realize what’s exposed. Through automated reconnaissance, asset discovery tools, and open-source intelligence, they’re thinking like red teamers, acting like bug bounty hunters, and exploiting gaps in real-time.
The good news is you can beat them at their own game.
This article explores how Sprocket Attack Surface Management Tool was built to understand the attacker playbook and reclaim visibility and control over your expanding attack surface.
Sprocket Security CEO, Casey Cammilleri, shares the difference between Sprocket ASM and other tools out there is “Seeing the hacker’s perspective and a heavyweight on change detection. What has changed from yesterday and does it impact my security? That’s how we’ve thought about building [Sprocket] ASM.”
The Attacker’s Perspective: Mapping Your Attack Surface
An attacker’s point of view of ASM mirrors that of a legitimate security professional, with gathering intelligence or discovery. Thanks to publicly available tools and automation, finding exposed assets, overlooked endpoints, and shadow IT is easier than ever for an attacker. Adversaries can quickly assemble a detailed map of your external-facing infrastructure.
In the Sprocket Security Red Teamers’ experience, most organizations unintentionally expose more than they realize. Legacy dev environments, abandoned domains, or forgotten SaaS integrations are all low-hanging fruits that attackers love. They can build their own ASM workflows using a combination of open-source tools, like Amass, and custom scripts to automate these findings at scale.
If an attacker has a more up-to-date or accurate map of your infrastructure than your own, that’s where the real danger lies.
Use Case: Broadcom’s VMware ESXi Vulnerability Exploits (2023-2024)
Threat actors launched mass exploitation campaigns against thousands of internetexposed VMware ESXi servers using known vulnerabilities.
These flaws were actively exploited in the wild, allowing attackers on a virtual machine with administrative privileges to escape the sandbox and execute code on the host system. Despite patches being available, over 37,000 internet-exposed VMware ESXi servers remained vulnerable, highlighting the risks of unpatched, publicly accessible assets.
“If it’s exposed to the internet, you better treat it like it’s already under attack. Continuously scan your external attack surface as if you’re the attacker. Flag any highvalue assets and then patch, isolate, or remove them. Don’t wait for the headlines. Act as soon as a vulnerability is disclosed before it’s exploited.” – Michael Belton, Head of Service Delivery at Sprocket Security.
Are you ready to see what a hacker would see if they had free reign over your attack surface?
Take the next step in becoming more secure by creating an account with Sprocket ASM.
Create Free Account
Sprocket ASM: Turning Recon into Prevention
If attackers can map your infrastructure, then you must do the same only faster, deeper, and continuously. Sprocket ASM Tool was designed to give you the same reconnaissance capabilities attackers rely on, but with context, validation, and continuous monitoring. Instead of manually going through asset inventories or reacting to alerts after the fact, you can use Sprocket ASM to see what attackers see in real time.
Cammilleri’s insights are “If you have ASM, you can spend less time in discovery phases and move straight into testing and validation phases. You will be more efficient and scalable in your offensive testing.”
Successful ASM isn’t just about visibility though. It’s about actionable insights. Many organizations miss key exposures because they rely too heavily on internal CMDBs or legacy inventories. By the time those systems catch up, attackers may already be exploiting an overlooked dev instance or forgotten S3 bucket.
The key to turning recon into prevention? Operationalizing ASM. Integrating it into daily workflows, connecting it with vulnerability management, and ensuring your team acts on exposures with the urgency that an attacker has already discovered them.
If you don’t monitor your digital infrastructure from the outside in, someone else will.
How to Get Started: Beat the Bad Guys to Your Blind Spots
Sprocket ASM Tool was created by penetration testers who understand attacker behaviors. Defenders need the same perspective and speed as their adversaries to stay secure. This no-cost tool delivers unparalleled visibility into your attack surface and provides insight into the evolving environment.
By revealing what attackers can exploit, our tool enables your team to act proactively and mitigate risks before they escalate.
“It’s the same engine that our red team and testers use in their continuous pentesting practice. You’re going to get notifications on new discoveries and changes,” shares Cammilleri, “But then you can seed the ASM with additional assets you own and manage.
If there’s something that an attacker would be totally blind to on the Internet, you could still feed in that information into the ASM and start tracking it for changes and security issues.”
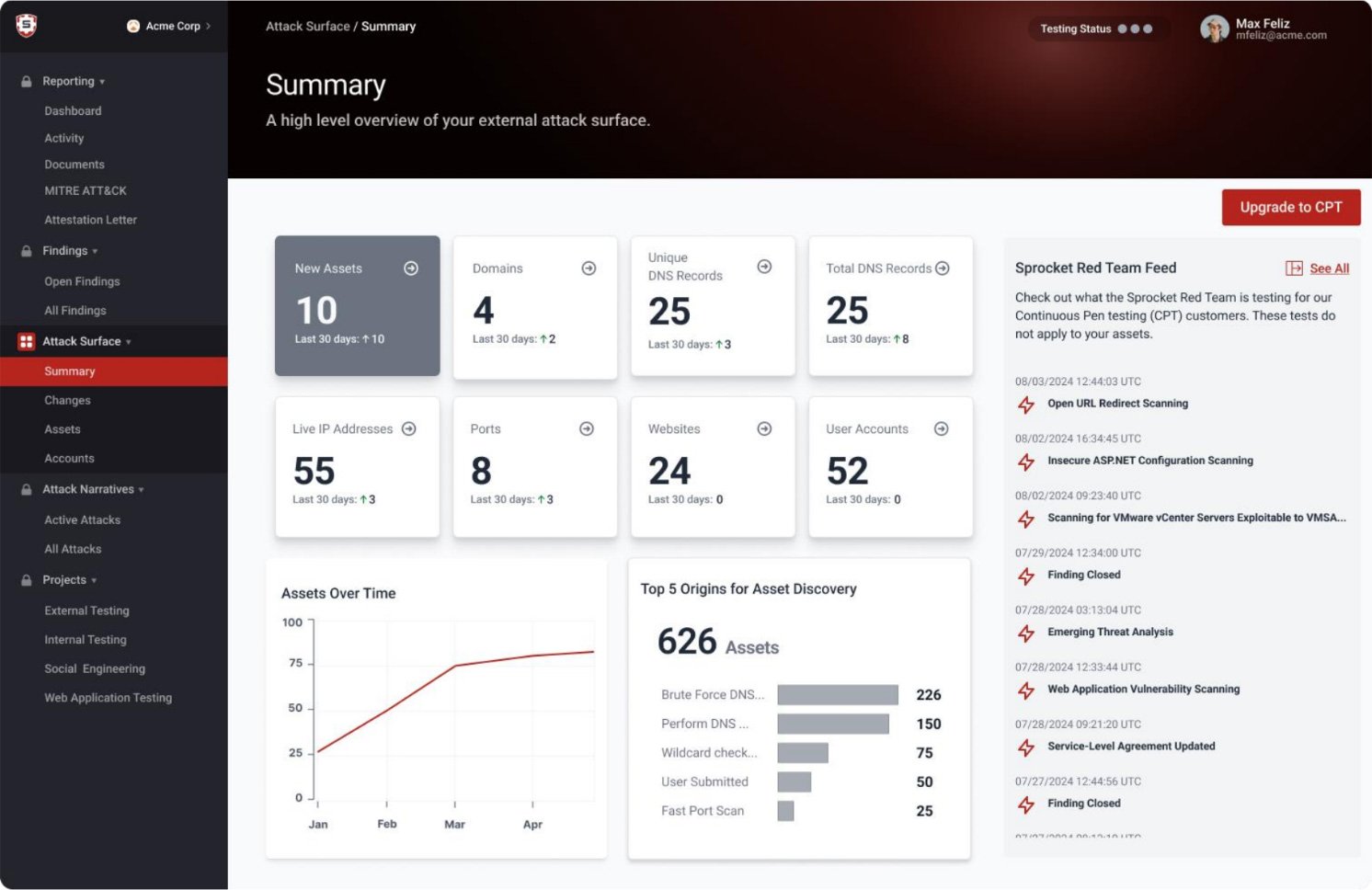
After creating your free account, you can:
✓ Discover all your exposed assets — domains, IP addresses, services, and much more — automatically.
✓ Cut through the noise and focus on what matters most with clear, actionable risk priorities.
✓ Gain control of your security posture with proactive asset discovery and effective management
Watch our comprehensive ASM tool demo to uncover even more benefits of utilizing Sprocket ASM.
Take the Offensive: Close Your Gaps
Attackers aren’t waiting for permission. They’re already scanning, mapping, and exploiting exposed assets. If you’re not looking at your attack surface the way an attacker would, you’re already at a disadvantage. You cannot secure what you don’t know exists.
Unknown assets, shadow IT, and misconfigured services are the weak links that attackers love to find, and traditional security tools often miss.
That’s why visibility is foundational. Use visibility to harden, not harm, by continuously discovering your external attack surface, prioritizing exposure by real-world risk, and closing gaps before adversaries exploit them.
With solutions like Sprocket ASM, you can stop playing catch-up and start seeing your infrastructure the way attackers do and that’s how you can beat them.
Sponsored and written by Sprocket Security.














