Threat actors are already trying to exploit a critical authentication bypass flaw in Progress MOVEit Transfer, less than a day after the vendor disclosed it.
MOVEit Transfer is a managed file transfer (MFT) solution used in enterprise environments to securely transfer files between business partners and customers using the SFTP, SCP, and HTTP protocols.
The new security issue received the identifier CVE-2024-5806 and allows attackers to bypass the authentication process in the Secure File Transfer Protocol (SFTP) module, which is responsible for file transfer operations over SSH.
An attacker leveraging this flaw could access sensitive data stored on the MOVEit Transfer server, upload, download, delete, or modify files, and intercept or tamper with file transfers.
Exploit code available
Threat monitoring platform Shadowserver Foundation reported seeing exploitation attempts shortly after Progress published the bulletin on CVE-2024-5806, so hackers are already attacking vulnerable endpoints.
Network scans by Censys indicate that there are currently around 2,700 internet-exposed MOVEit Transfer instances, most located in the US, UK, Germany, Canada, and the Netherlands.
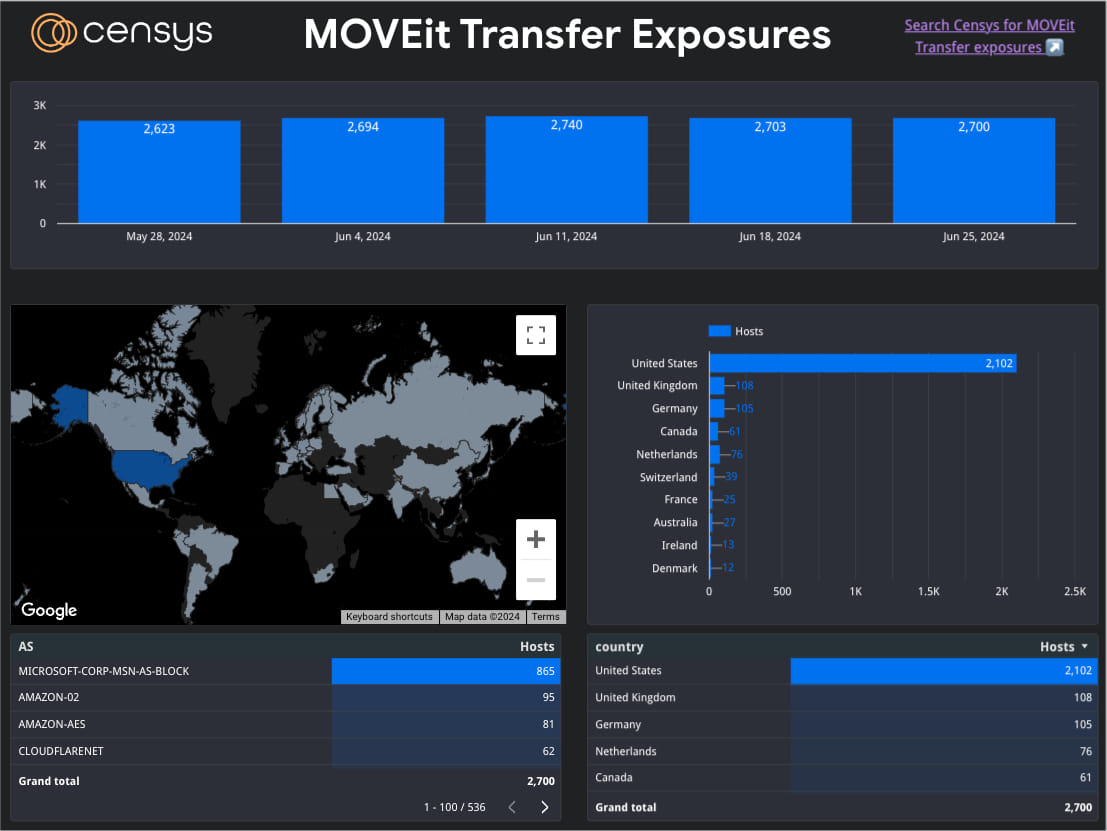
However, the percentage of those who haven’t applied the security updates and/or the proposed mitigations for the third-party flaw is unknown.
ShadowServer’s report of exploitation attempts comes after offensive security company watchTowr published technical details about the vulnerability, how it can be exploited, and what defenders should look for in the logs to check for signs of exploitation.
watchTowr also provides a technical analysis of how attackers can manipulate SSH public key paths to force the server to authenticate using attacker-controlled paths, potentially exposing Net-NTLMv2 hashes.
Additionally, proof-of-concept exploit code for CVE-2024-5806 is already publicly available from watchTowr and vulnerability researcher Sina Kheirkhah.
With this information out, the attacks will surely pick up pace in the following days, so it’s crucial for organizations to apply the related security updates and mitigations as soon as possible.
Patches released for CVE-2024-5806
As Progress explained in the security bulletin, CVE-2024-5806 impacts the following product versions:
- 2023.0.0 before 2023.0.11
- 2023.1.0 before 2023.1.6
- 2024.0.0 before 2024.0.2
Fixes were made available in MOVEit Transfer 2023.0.11, 2023.1.6, and 2024.0.2, available on the Progress Community portal.
Customers without a current maintenance agreement should immediately contact the Renewals team or Progress partner representative to resolve the issue.
MOVEit Cloud customers do not need to take any action to mitigate the critical flaw, as patches have already been automatically deployed.
In addition to the flaw itself, Progress notes that it discovered a separate vulnerability on a third-party component used in MOVEit Transfer, which elevates the risks associated with CVE-2024-5806.
To mitigate this flaw until a fix from the third-party vendor is made available, system administrators are advised to block Remote Desktop Protocol (RDP) access to the MOVEit Transfer servers and restrict outbound connections to known/trusted endpoints.
Progress also released a security bulletin about a similar authentication bypass issue, CVE-2024-5805, which impacts MOVEit Gateway 2024.0.0.
MOVEit is widely used in the enterprise environment and hackers are keeping a eye on vulnerabilities and exploits available on the product, especially since Clop ransomware leveraged a zero day last year to breach and subsequently extort thousands of organizations.














