X-VPN, operated by LIGHTNINGLINK NETWORKS PTE. LTD. has shared an update on so-called path-signal attacks (often called Blind In/On-Path in research). The company outlines what it verified in controlled tests, how it’s working with platform vendors, and what everyday users can do right now.
The quick version
- No plaintext data found outside the encrypted tunnel in X-VPN’s controlled tests.
- Signals observed are tied to how some operating systems handle traffic by default, not to broken VPN encryption.
- X-VPN submitted test artifacts and timelines to Google via official security channels.
- Linux filtering shipped to cut down on unwanted probe traffic at the tunnel interface.
- Android mitigations under evaluation (app-level, non-root), with caution about stability/performance tradeoffs.
- A third-party review of logging enforcement, encryption behavior, and tunnel integrity is in progress.
What this actually means
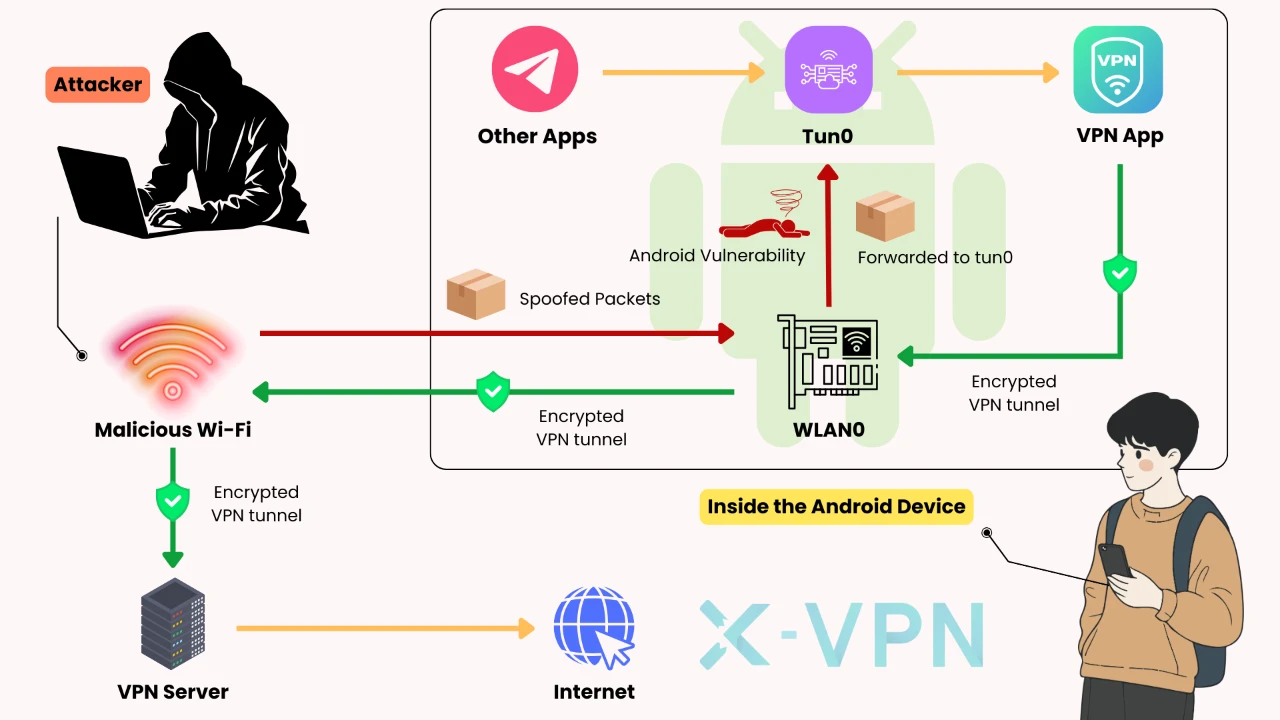
On an unsafe Wi-Fi (think: a rogue hotspot), an attacker can send small “test” packets and watch whether a device reacts. From those reactions, they may guess you’re on a VPN, or try to interrupt the connection. This is traffic behavior—not decryption. Your messages remain encrypted.
In practice, the playbook has two steps:
- Identification — probing for tell-tale reactions;
- Disruption — attempting to reset or disturb an active session. Encrypted content isn’t revealed by these probes.
How X-VPN tested (and why it matters)

To avoid product bias, engineers ran the same checks across multiple operating systems and repeated them with several well-known VPN apps under similar conditions. Results, timestamps, and logs were shared with Google through its official security intake. For safety, step-by-step instructions that could enable abuse are not published.
What X-VPN saw (grouped by signal type, not by brand)
Clearly observable under specific conditions
In scenarios linked to certain Android defaults, crafted probes can trigger device-level reactions that outsiders can measure. Because app-based VPNs on Android use the VpnService API and don’t control kernel networking, closing the gap fully requires OS-level rule changes from the platform vendor.
Configuration-dependent
On Linux, similar effects can surface when routing/filters are permissive. Since Linux allows tighter system rules, the current X-VPN client now drops unexpected packets at the tunnel interface to shrink what can be observed on hostile networks.
Not reproduced as an equivalent pattern
Within X-VPN’s documented scope and public literature review, iOS, macOS, and Windows did not show the same stable signal.
What’s shipping and what’s next
Coordinated disclosure
Artifacts, reproduction notes, and dates have been submitted to Google to support platform-level assessment.
Linux hardening
Interface-level filtering is live to discard unsolicited traffic before it can provoke a response.
Android work
Non-root, app-layer heuristics are in testing to soften probe effects; they can help in some cases but cannot replace system rules.
Independent review
A third-party assessment covering no-logs enforcement, encryption behavior, and tunnel integrity is underway. A public summary will follow.
For a more detailed guide, you can check the Official Statement from X-VPN regarding Blind In/On-Path Attacks here.
What readers can do today (fast wins)
- Use trusted Wi-Fi or cellular data for sensitive tasks; avoid unknown hotspots.
- Update your OS and the X-VPN app to pick up platform security improvements.
- On Android, enable the Kill Switch (available to all users, including free tier) so traffic is blocked if the VPN disconnects.
- Prefer HTTPS in apps and browsers; avoid sending sensitive info over HTTP.
- If you notice frequent disconnects or odd redirects, pause sensitive activity and leave that network.
- For IT teams, combine endpoint rules with gateway filtering to discard spoofed or out-of-policy traffic and log events for review.
Why X-VPN is publishing this now
Recent academic discussion—and some public confusion—sparked questions about what’s actually at risk. X-VPN’s goal is to separate what is reproducible from what is not, publish user-actionable guidance, and press for platform updates where system defaults contribute to the signals.
Timeline snapshot
Early Oct 2025 — Internal investigation and controlled reproduction begin.
Mid-Oct 2025 — Findings documented; artifacts sent to Google.
Now — Linux filtering shipped; Android heuristics under evaluation; independent review in progress.
About X-VPN
X-VPN is operated by LIGHTNINGLINK NETWORKS PTE. LTD. in Singapore. The service supports multiple tunneling options — WireGuard, OpenVPN, and the Everest family — with modern encryption and session protections, backed by a global network of 1,000+ servers.
Media Contact: support@xvpn.io
Source: X-VPN
Latest viraltrendingcontent Gadgets Deals
Disclosure: Some of our articles include affiliate links. If you buy something through one of these links, viraltrendingcontent Gadgets may earn an affiliate commission. Learn about our Disclosure Policy.













