Google has fixed a high-severity Chrome zero-day vulnerability exploited to escape the browser’s sandbox and deploy malware in espionage attacks targeting Russian organizations.
“Google is aware of reports that an exploit for CVE-2025-2783 exists in the wild,” the company said in a security advisory published Tuesday.
Tracked as CVE-2025-2783, this vulnerability was discovered by Kaspersky’s Boris Larin and Igor Kuznetsov, who described it as an “incorrect handle provided in unspecified circumstances in Mojo on Windows.”
Google fixed the zero-day for users in the Stable Desktop channel, with patched versions rolling out worldwide to Windows (134.0.6998.178) users. Although the company says the security update will roll out over days and weeks, it was immediately available when BleepingComputer checked for updates.
Users who prefer not to update Chrome manually can let the browser automatically check for new updates and install them after the next launch.
While it tagged CVE-2025-2783 as exploited in attacks, Google has yet to share further details regarding these incidents and said that “access to bug details and links may be kept restricted until a majority of users are updated with a fix.”
However, Kaspersky researchers who discovered the actively exploited zero-day also published a report with additional details, saying that attackers use CVE-2025-2783 exploits to bypass Chrome sandbox protections and infect targets with sophisticated malware.
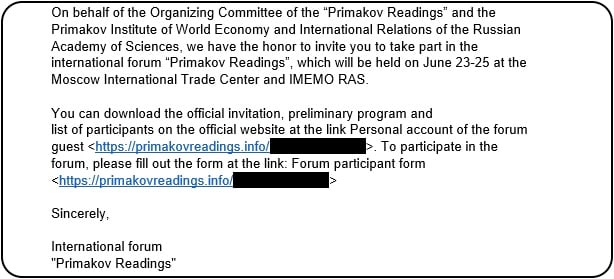
The vulnerability is now being exploited in phishing attacks, redirecting victims to the primakovreadings[.]info domain as part of a cyber-espionage campaign targeting Russian organizations, dubbed Operation ForumTroll.
While analyzing these attacks, Kaspersky researchers found that the attackers also used a second exploit that enabled remote code execution on compromised systems. Although no information on this additional exploit is available, patching Chrome will disable the entire exploit chain and block potential attacks.
”While research is still ongoing, but judging by the functionality of the sophisticated malware used in the attack, Kaspersky says the attackers’ goal was likely espionage,” Kaspersky said.
“The malicious emails contained invitations supposedly from the organizers of a scientific and expert forum, ‘Primakov Readings,’ targeting media outlets, educational institutions and government organizations in Russia. Based on the content of the emails, we dubbed the campaign Operation ForumTroll.”
CVE-2025-2783 is the first Chrome zero-day patched since the start of 2025. Last year, Google patched 10 zero-days, either exploited in attacks or demoed during the Pwn2Own hacking contest.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.














